
As we bid farewell to 2022, it's time to look back to see how the IT and cybersecurity landscape has shifted over the past year. Security professionals faced various new challenges, while some long-standing security issues continued to affect organizations worldwide.
Forewarned is forearmed. Take a look at the landscape of the last year to take a proactive approach in 2023 and beyond.
As countries around the globe continue and accelerate their digital transformations post-pandemic, it has become increasingly apparent that there is a major gap in the workforce regarding cybersecurity – a problem that, if left unchecked, could start to threaten the advancement of digital technologies and infrastructure.
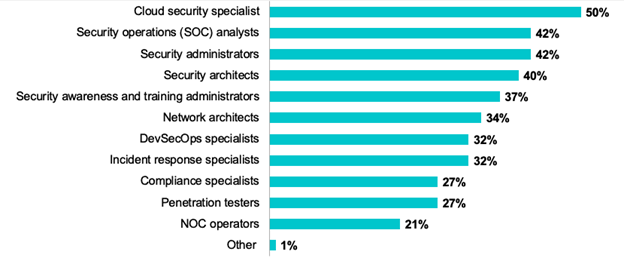
Looking at current hiring trends, it appears that cloud security architects and specialists are in high demand, with more than half of organizations needing these roles to ensure their own cyber protection.
At the same time, this increased demand for qualified cyber defenders also hints at a shift in attitudes towards cybersecurity amongst businesses and governments. As the digital landscape continues to evolve, greater emphasis is being placed on protecting sensitive information, systems, networks, and personnel from sophisticated cyber threats.
The global supply chain has undergone a fundamental shift over the past few years. The global pandemic caused massive disruptions and delays in supply chains due to the withdrawal of personnel, lack of resources, transportation issues, and other factors. This has led to many new challenges to an already hindered supply chain.
At the heart of this is an alarming number of incidents where malicious actors have taken advantage of vulnerabilities in an organization's supply chain to gain access to sensitive data. Threat actors can effectively act as a force multiplier by compromising a single partner, exploiting multiple downstream firms in quick succession.
As most organizations have adapted to highly remote workforces and operations, there is also an increase in social engineering attacks that take advantage of the complex global supply chains, often preying on overseas suppliers and other third-party vendors. In an industry that involves multiple partners and providers, it’s vital that everyone has a consistent approach to cybersecurity and awareness.
Insider threats are one of the most difficult cyberattacks to detect and prevent. In 2022, more organizations recognized that malicious insiders are a real threat and took proactive measures to protect their data.
Organizations have introduced security automation tools such as user behavior analytics (UBA) systems to monitor employee activities and detect suspicious activity. They have also been taking steps to increase employee awareness and education of potential insider threats and tightening access controls across the organization's networks and systems. This has been a critical effort as businesses hire younger generations of workers accustomed to using multiple devices and cloud-based services.
Zero Trust is quickly becoming the go-to cybersecurity framework for organizations seeking to protect their networks and data. The concept of Zero Trust requires organizations to verify the identities of users attempting to access sensitive areas or resources, regardless of where they are located. This ensures that only authenticated and authorized users can access protected data and systems.
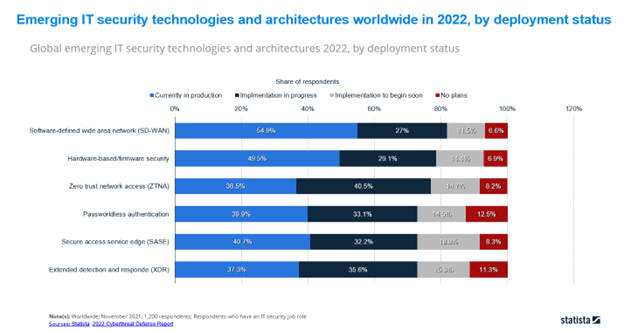
Organizations are increasingly adopting Zero Trust principles to protect their networks and data from malicious actors. They are also leveraging identity management solutions, such as multi-factor authentication (MFA), to ensure that only legitimate users can access sensitive systems.
In the future, more organizations will continue to adopt Zero Trust principles as they become further aware of the potential threats posed by malicious actors. This will increase the security of their networks and data and offer greater peace of mind to those responsible for protecting them.
As cybercriminals become increasingly tech-savvy, the threat of deepfake technology is becoming ever more real. The FBI has already reported attempts to combine BEC techniques with deepfakes and video conferencing software, leading to cases of fraud through audio fakes. Now, with the advances in technology and lowering price points, there is an increasing risk of video fakes being used. This could be immensely damaging if distributed via Zoom calls or other means of communication.
To stop this from happening, businesses must take steps to protect themselves from this type of attack. Firstly, employees should be better trained in spotting deepfake attacks, and procedures for signing off on wire transfers should be improved. Secondly, utilizing AI-powered tools can help to detect and block such malicious content before it reaches its intended victims. By staying alert and taking appropriate measures, businesses can go a long way toward preventing fraud via deepfake technology.
In 2022, data breaches were more frequent and costly than ever. According to InfoSecurity Magazine, there was a massive 70 percent rise in data breaches in Q3 of 2022 compared to 2021. This demonstrates the importance of keeping up with the latest security measures if businesses are going to protect their data from malicious attacks.
If businesses want to reduce their risk of a breach and decrease its costs when one occurs, they must take proactive steps towards strengthening their defenses against adversaries. Security solutions like firewalls, antivirus software, and user education are critical tools for staying ahead of threats. Businesses should also work on establishing disaster recovery plans and regularly testing them so that they can respond quickly once a breach happens.
With the right security postures in place, businesses can reduce their risk of a data breach, and if one occurs, limit its associated costs and ramifications.
As we move into 2023, it is essential that organizations continue to prioritize their cybersecurity strategies and remain vigilant against new threats. While technology and security practices have certainly advanced in recent years, it is still important to remain informed on the latest trends and keep up with the best practices to prepare for what lies ahead.