
There is no shortage of challenges that small businesses face as they begin to find their way in the market. From closely managing their finances to scaling their operations, every decision a small business makes or fails to make can seriously impact its long-term viability.
But, like most modern businesses, one area that plays a significant role in the scalability and sustainability of an organization’s operational state is its underlying infrastructure. And IT is critical to ensuring a business’s foundation can weather the storm in today’s hostile digital environment.
However, there are many IT challenges that small businesses face when setting up critical infrastructure, and recognizing these challenges early can help you avoid common pitfalls that organizations fall into.
While many small business owners may have an idea of how they would like their organizations structured when it comes to establishing the company’s basic operations and the technology that supports it, businesses often lack a dedicated strategy for managing it all properly.
This usually results in sporadic purchases of expensive hardware or software solutions in an effort to quickly move the company forward. However, without a long-term IT strategy in place, usually the reverse happens. As a result, businesses can quickly find themselves over budgeting non-essential purchases while dedicating their resources to the wrong areas.
The cybersecurity landscape has evolved considerably over the last several years and only continues to put more pressure on businesses to keep pace. Small businesses especially are at high risk of being targeted by malicious outsiders due to a lack of awareness or adequate budgeting towards their cybersecurity initiatives.
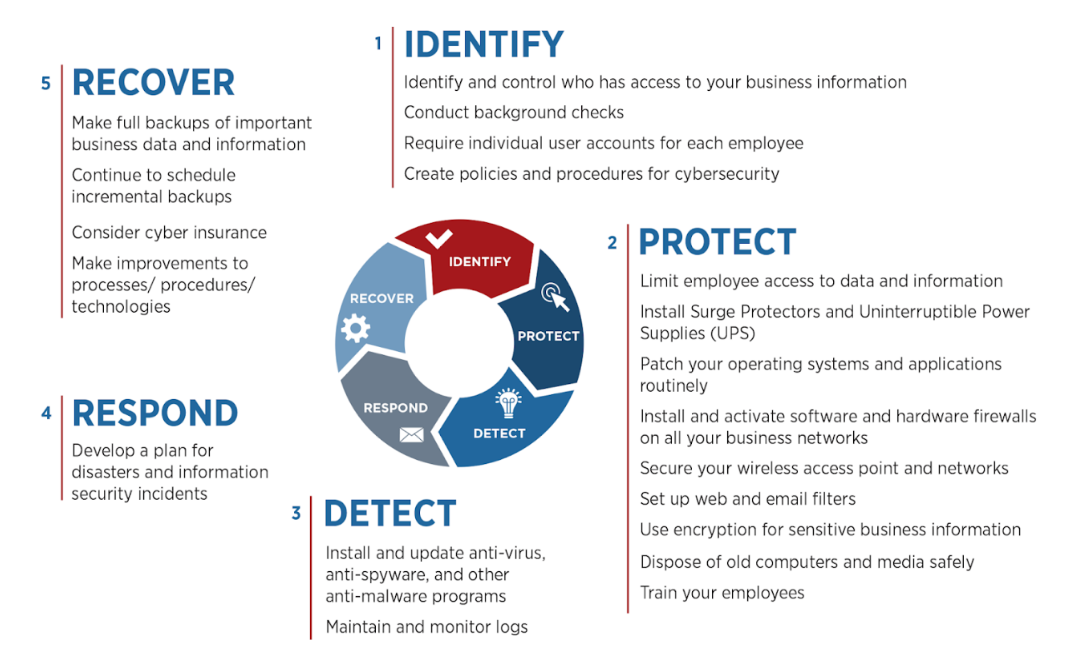
Implementing cybersecurity frameworks like NIST (National Institute of Standards and Technology) into business strategies is critical to minimize the organization’s attack surface and harden its security protocols. Lacking adequate controls and proper SOP (Standard Operating Procedures) documentation is a dangerous but common issue small businesses face.
Another challenge businesses face when not implementing the right security standards from the start is that they often neglect adequate employee security training. While employees are a company’s greatest assets, especially as an organization begins to grow, they can also become a higher risk to business security.
If employees lack awareness of the importance of business security and the part they play in helping to mitigate security risks, there can be serious consequences for the organization as a whole. Prioritizing cybersecurity training and ensuring that employees regularly learn, review and accept key policies surrounding the continuous protection of company and client data will help to significantly reduce the likelihood of compromised credentials, data breaches, or compliance issues.
No matter the size, businesses generate a lot of data – and it’s usually all over the place. Whether communicating on messenger applications and through email or tracking customer leads through CRM (Customer Relationship Management ) and ERP (Enterprise Resource Planning) platforms, it’s easy to lose track of how many places critical business data lives.
This can become a major issue, especially when managing important client information, vendor contracts, and other sensitive business information. Therefore, businesses must take the time to build the right systems for managing their disparate data and create smart integrations that can streamline data exchanges.
This not only helps maintain regulatory compliance standards but can also be a great way to increase efficiency and productivity in the organization.
If COVID-19 has taught us anything over the last three years, businesses need to be prepared for anything. But pandemics aren’t the only thing that can disrupt a business’s day-to-day operations.
Natural disasters, unplanned system outages, and cybersecurity breaches can lead to costly downtime in an organization, leading to disastrous financial consequences for small businesses.
While not all of these situations can be avoided, businesses can minimize their impact by implementing a comprehensive disaster recovery plan. These plans outline everything from critical systems and protocols to the staff responsible for ensuring they’re fully recovered.
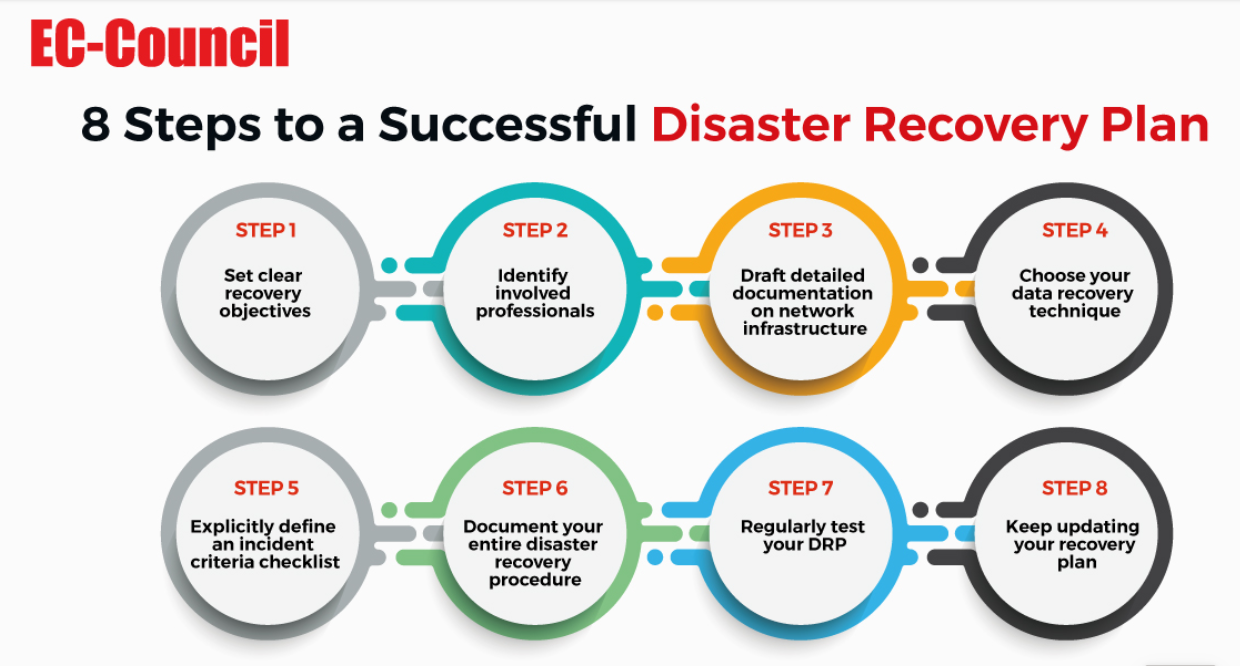
Third-party solutions providers play a crucial role in ensuring data backups are safely stored and used during an outage or major security incident. Without these critical recovery plans, it could spell disaster for an organization if something were to impact daily operations for an extended period.
Although most small businesses tend to be more reactive when addressing their IT issues, primarily due to budgeting constraints, maintaining this mentality long-term can lead to costly consequences.
Break-Fix IT models are an all-too-common principle in smaller business environments. Break-Fix essentially refers to the “wait till it breaks” method of handling IT issues. The primary reason for this is that it limits a lot of the upfront spending on expensive hardware or software that only brings a certain percentage of value to the organization in the short term.
While this can be a more economical IT model when things are going well, it can lead to costly problems down the road‒ones that the organization didn’t originally budget for.
Proactive IT management and planning is often the best route to take, as it helps the business better understand its short- and long-term priorities regarding the scalability and sustainability of its operations.
As a business grows, so does its staff count. And while many organizations have their own process for acquiring and retaining their staff, many still don’t have adequate checklists in place when it comes to their onboarding and offboarding procedures.
Onboarding and offboarding procedures are an absolute must for keeping the business protected. It is vital to know what systems employees have access to from the start and efficiently close those access points when they exit.
Maintaining a comprehensive policy for how your in-house or remote employees are managed, including what equipment they are assigned and the access levels they’ve been granted, will help you quickly and efficiently address issues as they arise and ensure safer security protocols.
Depending on what industry your business is in, it is often subject to any number of regulatory business requirements that outline everything from how you should be handling your customer’s data to how you notify them in the event of a security breach.
Not understanding these regulatory requirements can have serious legal ramifications, including severe government fines for non-compliance and debilitating lawsuits from customers if their information is compromised.
On top of this, not fully understanding your business’s compliance requirements can also make it more challenging, if not impossible, to implement any type of cybersecurity insurance. This can be a significant issue for small businesses often targeted by ransomware or attacks designed to halt operations completely.
It’s imperative that businesses partner with the right IT providers and consultants who can adequately assess their operational state and advise on the best course moving forward.
For every small business, IT roadblocks are commonplace. There are always things that can be improved, and you should not be discouraged when discovering that some of your systems and processes are lacking.
However, by staying vigilant, identifying industry best practices, and relying on the expertise of IT service providers, you’ll successfully identify these challenges as they occur and put in place optimal resolutions to ensure your business is better positioned for growth and long-term viability. LDD has been the trusted IT Company in Albuquerque that local businesses rely on for expert guidance and reliable support. Schedule your complimentary 10-minute consultation to discuss your organization’s IT health.
If you are wondering about the IT health of your organization or have any questions, contact LDD for a complimentary 10-minute phone consultation. David Luft is the owner and CEO of LDD Consulting and has been supporting small businesses in Albuquerque since 2003. We’re happy to chat with you about your business.